The Skyrocketing Risk of Data Breach and Social Networks
Verizon released a 2014 Data Breach Investigations Report (DBIR) which examined 63,000 global suspected data breach incidents in 2013.
The report found that over 90% of all data breaches worldwide can be placed in 1 of 9 distinct categories. This is an important step in cataloguing and defining the sources of data risk so that organizations can better identify which of these 9 categories they may be vulnerable to, and from there develop a coherent risk strategy.
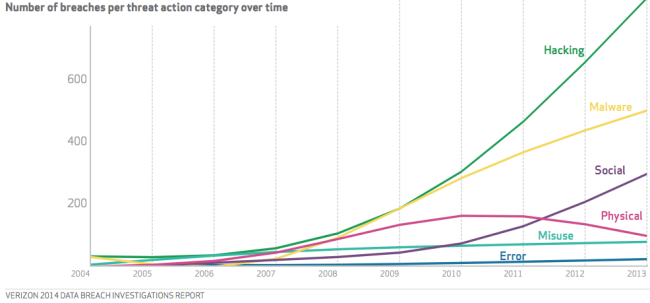
One interesting graphic in the report looked at trends of the threat vectors. In other words, how do cyber criminals actually extract data from victims, and how do their broad tactics change over time.
Since 2007, both hacking and malware have been the most popular vectors to access information. Hacking into systems or installing malware on a network or computer was overwhelmingly the most common way a data breach would occur.
However, since 2010 “social” data breaches are skyrocketing, and are now the 3rd most common vector for criminals to access data, and “social” data breaches are on track to overtake malware as the 2nd most common attack vector.
Generally, “social” causation of data breach includes any one of the following as example.
- Stealing passwords from people using web-connected public computer terminals or point-of-sale devices
- Phishing scam emails designed to trick people into logging into fake sites which spoof a real banking or personal account
- SMS text messages purporting to be from a financial institution asking the recipient to reply with personal or login information
Passwords, usernames, emails, credit card, debit card, financial account numbers, social security and drivers license numbers are all primary targets in social data breach schemes, and the proliferation of smartphones, web-connected point-of-sale devices, banking or other financial transactions conducted through SMS texting, etc., are huge vulnerabilities.
The reason for the increase in data breaches from “social” systems makes sense. Only recently did consumers have access to smartphones and web-connected devices with them 24/7, and web-connected devices and systems are only recently being integrated into retail, banking and consumer establishments.
As social methods continue to increase as the cause of data breach, organizations need to implement safety measures into their risk plans. Does your company have policies dictating encryption, passwords, or usage for employee issue smartphones or tablets? Are your employees generally educated about the dangers of using company issued devices on public WiFi networks? Do company email networks aggressively identify and remove spam or phishing emails? These are the basic steps needed to be taken as part of any comprehensive risk management strategy.
Subscribe Now
Learn from the pros about risk-mitigation, document tracking, and more, with expert articles from bcs.